PROXIMANOVA-LIGHT.OTF PROXIMANOVA-LIGHTIT.OTF PROXIMANOVA-EXTRABLD.OTF PROXIMANOVA-BOLD.OTFPROXIMANOVA-BLACK.OTF
Get this font in here!
This Article Applies to:
- Avast Small Business Solutions
- Avast Small Office Protection
Ransomware Shield helps secure your personal photos, documents, and other files from being modified, deleted, or encrypted by
Note that Ransomware Shield is not a ransomware decryption tool - it is designed to prevent the infection by protecting your files and folders, but it cannot decrypt files already encrypted by ransomware. To get our free ransomware decryption tools, see this Avast page.
Ransomware Shield can be accessed from the Protection section of the client UI.
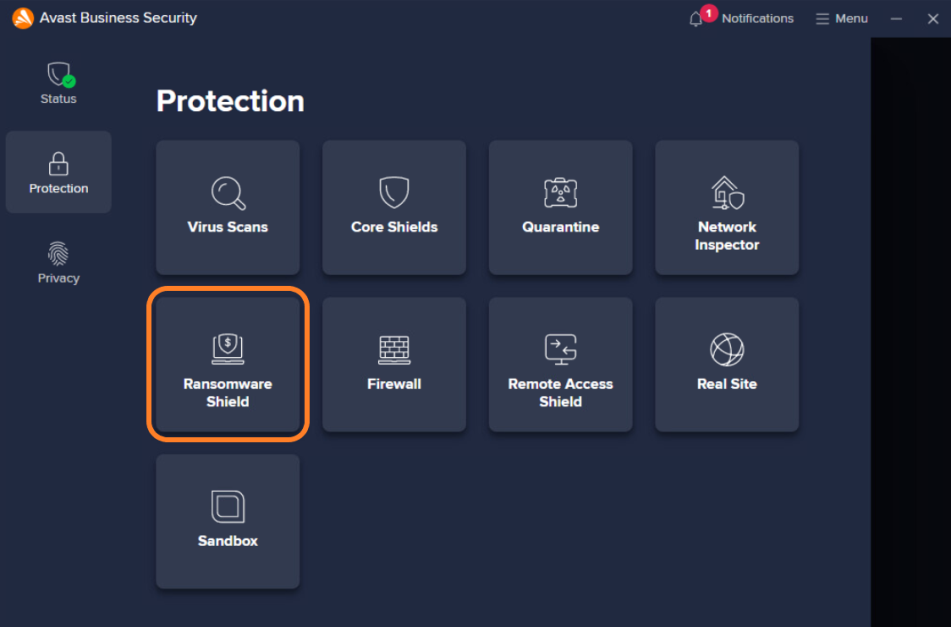
On the Ransomware Shield screen, you can enable/disable the component, see the existing protected folders and add new ones (see below), and access the advanced settings (gear icon). You can also use the Block or Allow App option to directly access the Blocked & Allowed Apps section of the settings (see Blocked & Allowed Apps below for more information).
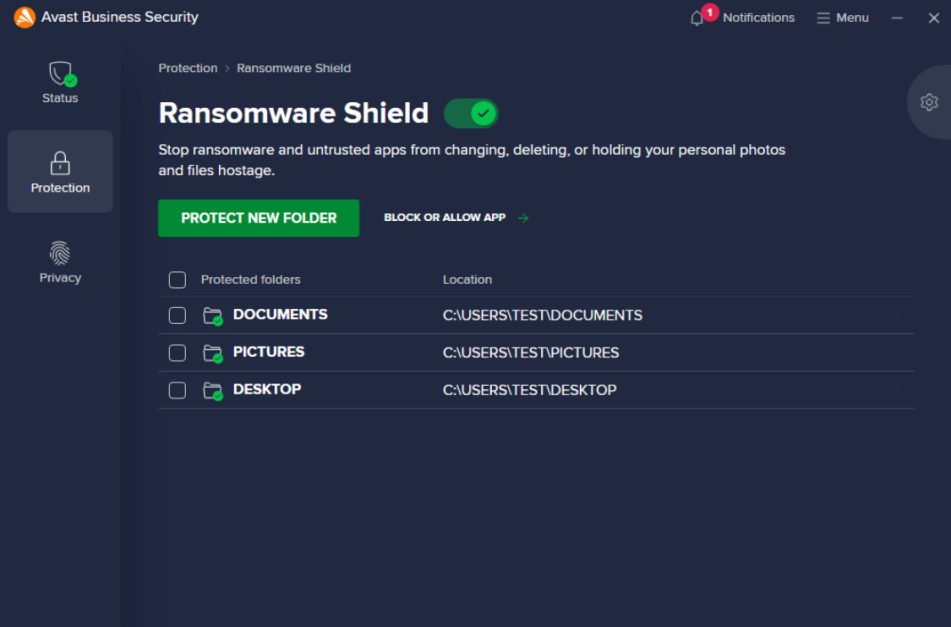
Specifying Protected Folders
By default, Ransomware Shield scans for and secures folders where your personal data might be stored (documents, pictures, desktop). To manually add folders to the list, click the Protect New Folder button, select the desired folder(s), then click OK.
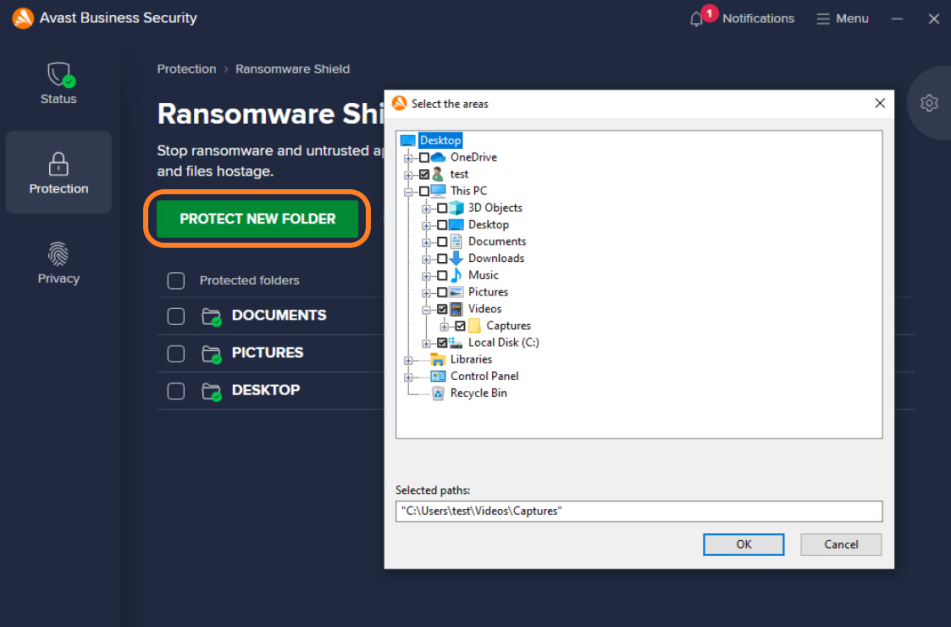
Holding the cursor over an existing entry will show the option to Stop protecting.
Clicking the X will open a pop-up dialog to confirm or cancel the action.
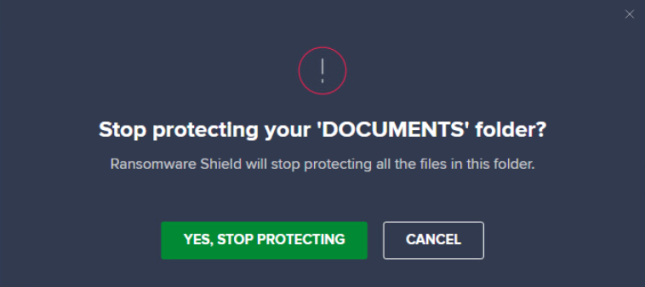
If you want to remove several folders from the list, the easier way would be ticking the checkboxes next to those folders, then clicking Stop Protecting.
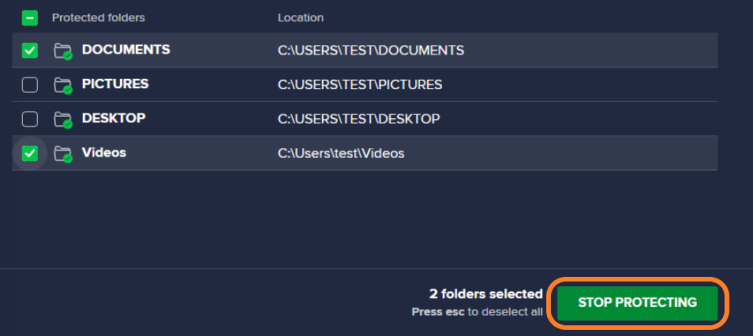
Configuring Ransomware Shield Settings
Advanced Ransomware Shield settings can be accessed by either clicking the gear icon on the Ransomware Shield screen or navigating to Menu > Settings > Protection > Ransomware Shield.
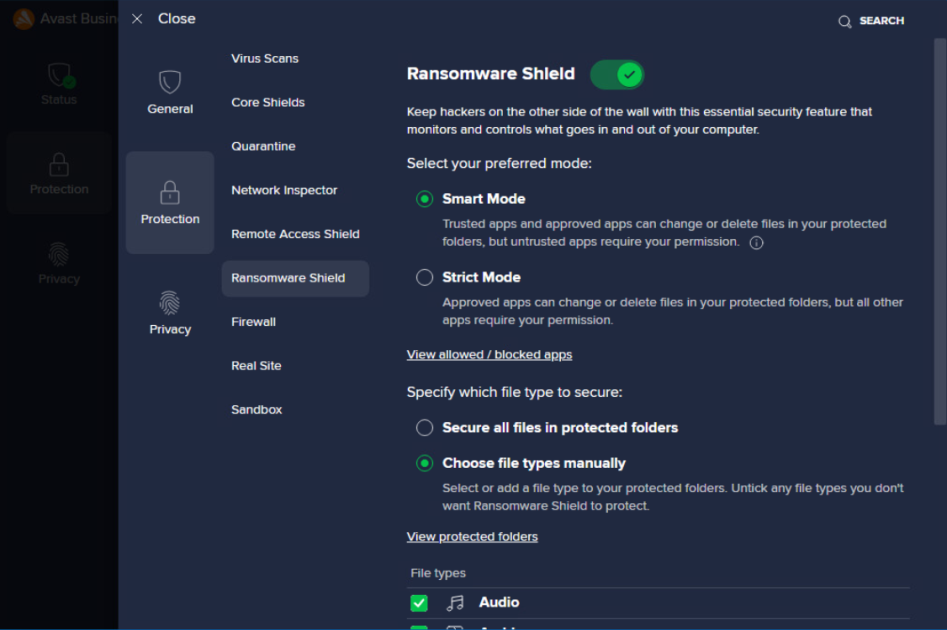
The following options are available here:
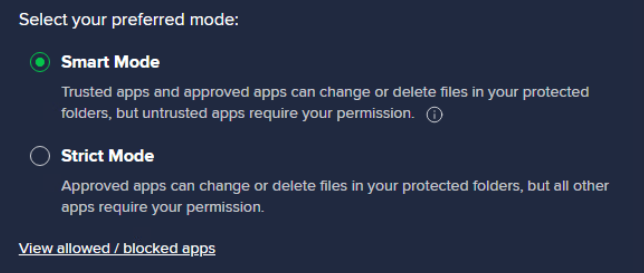
- Modes: Choose whether the Ransomware Shield mode is Smart (allows well-known trusted and approved applications to access protected folders, but needs your permission for allowing any untrusted ones) or Strict (allows approved apps and requires your permission for all unapproved ones).
- Clicking the View allowed / blocked apps link will bring you to the Blocked & Allowed apps list (see Blocked & Allowed Apps below).
- File types: Choose whether Ransomware Shield secures all file types in protected folders or only those you specify (select from the available options and/or manually add extensions under Additional file types to protect).
- Clicking the View protected folders link will bring you to the Ransomware Shield screen (see Specifying Protected Folders above).
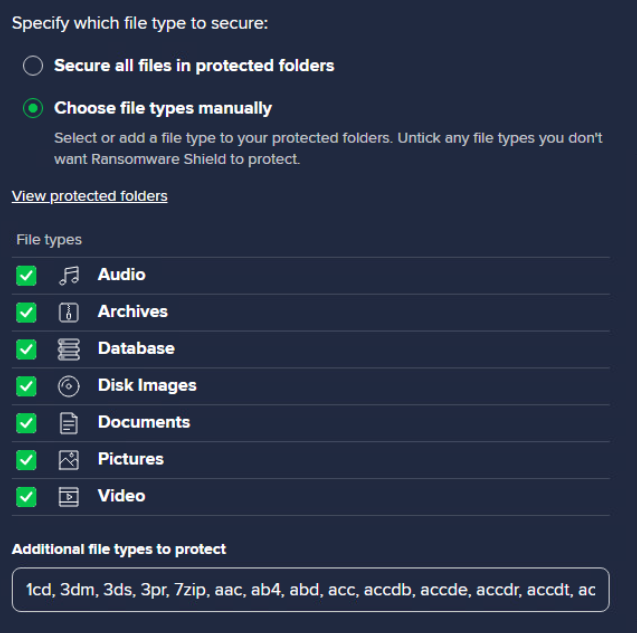
Blocked & Allowed Apps
As previously mentioned, clicking the View allowed / blocked apps link at the bottom of the Modes settings or the Block or Allow App button on the Ransomware Shield screen will bring you to the Menu > Settings > General > Blocked & Allowed apps section of the client UI, used by Ransomware Shield, as well as Webcam Shield, Sensitive Data Shield, and Browser Shield.
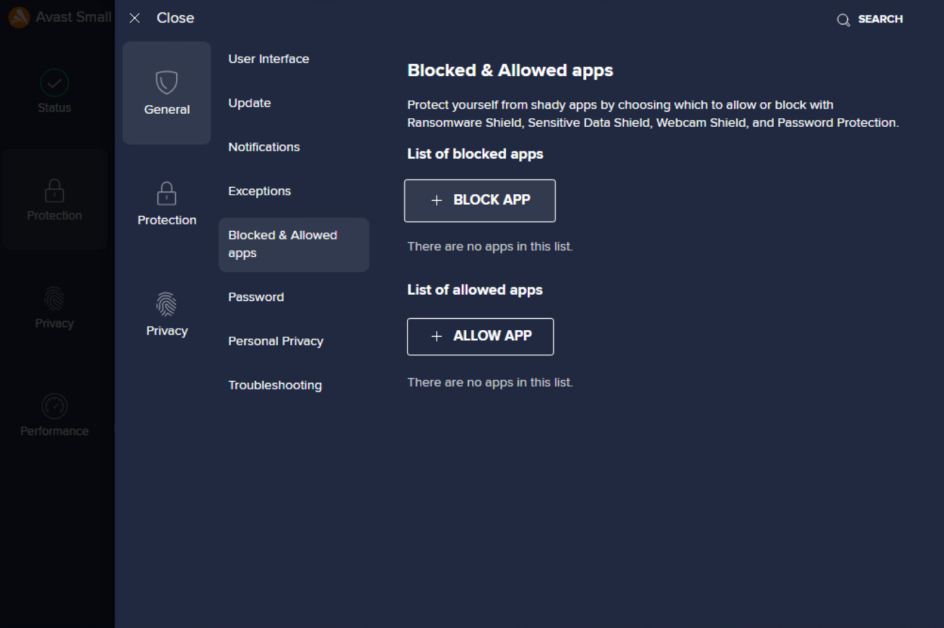
Here, you can configure individually each application that will be blocked/allowed and include whichever of the available shields/components. Rules set here will override the general configuration.
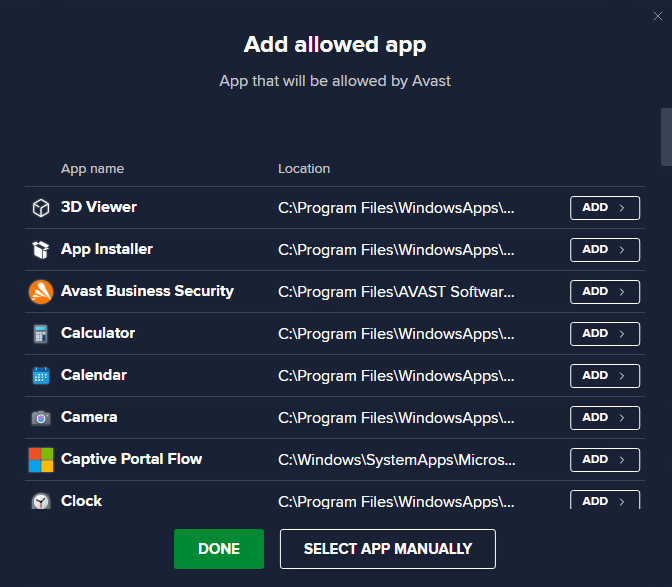
Clicking Block App or Allow App will open a dialog where you can either choose an active application directly from the list or click Select app manually to navigate elsewhere on the disk.
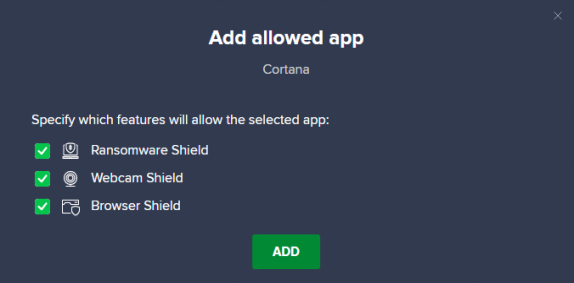
Once you select an app, define which shields/features are applied for that app, then click Add.
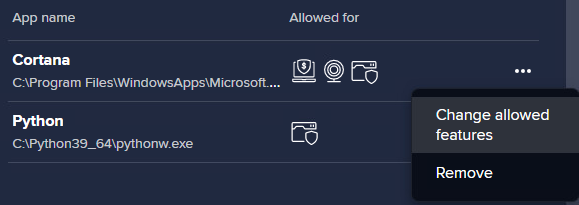
On the Blocked & Allowed Apps list, you will see the added applications and which components they apply to. You can edit or remove any listed app via its actions menu (three dots).
FAQ
 Does Ransomware Shield support protecting files on a network share?
Does Ransomware Shield support protecting files on a network share?
Not at this time. Network paths cannot be protected by Ransomware Shield. However, it is possible to define an application from a network path as trusted to allow it to access protected folders.
 Can Ransomware Shield decrypt files encrypted by Ransomware?
Can Ransomware Shield decrypt files encrypted by Ransomware?
No, users can try to use the decryption tools here.
 Are variables supported in Ransomware Shield settings?
Are variables supported in Ransomware Shield settings?
Yes - the user/administrator can use variables including %userprofile% to configure their protection.
 What happens if an attacker uses an exploit in a known trusted app and the user has smart mode/allow all trusted apps known by Avast enabled?
What happens if an attacker uses an exploit in a known trusted app and the user has smart mode/allow all trusted apps known by Avast enabled?
Other shields would take over at this point to prevent harm to the device (e.g. Anti-exploit Shield, File Shield, Behavior Shield).
 What should the admin do if access is allowed by the user for an application they don't recognize/don't wish to allow?
What should the admin do if access is allowed by the user for an application they don't recognize/don't wish to allow?
The administrator should contact the user and/or remove the application where required. They can also enable Silent mode in their settings which will silently block any non-allowed app without user interaction.
 Can you protect a whole local disk with Ransomware Shield?
Can you protect a whole local disk with Ransomware Shield?
No, system folders are not supported, therefore you cannot protect the whole disk.
 Can you protect removable drives?
Can you protect removable drives?
No, only local disks.
Other Articles In This Section:
Security Browser Extension (Avast Online Security & Privacy)
Services Available via Business Hub Only
Related Articles: