PROXIMANOVA-LIGHT.OTF PROXIMANOVA-LIGHTIT.OTF PROXIMANOVA-EXTRABLD.OTF PROXIMANOVA-BOLD.OTFPROXIMANOVA-BLACK.OTF
Get this font in here!
This Article Applies to:
- Avast Business On-Premise Console
Sandbox is a virtualization tool in Avast Business Antivirus that allows you to browse the web or run applications in a virtual, safe environment that is completely isolated from the rest of your PC's system. This feature is useful when you want to run suspicious or untrusted applications without risk.
When you run an application in Sandbox, all necessary files are always copied to Sandbox storage where they can be modified as needed without affecting the original files. Any new files created during virtualization are also saved to Sandbox storage. Sandbox storage is a file space completely isolated from the rest of your system and other Sandboxes. By default, Sandbox storage is created in the same drive as the original file.
Sandbox is not available for macOS devices.
Configuring Sandbox Settings
To access Sandbox settings:
- Open the Policies page
- Click the desired policy to open its settings
- Select Windows Workstation or Windows Server
- Go to the Active protection tab
- Click the Customize link next to Sandbox
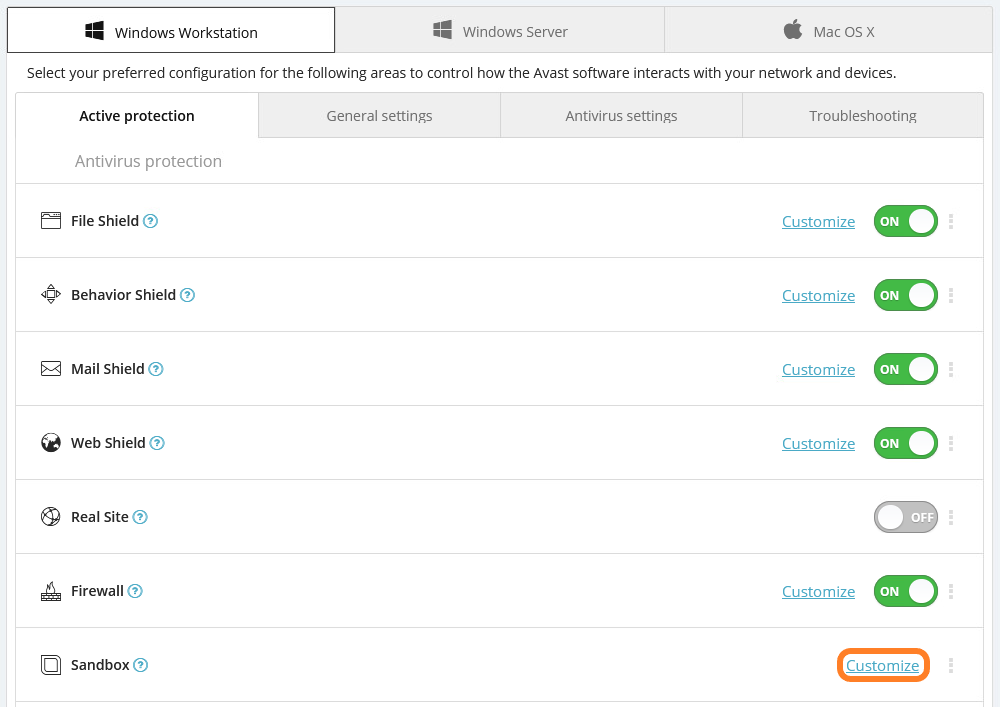
The available configuration options will be split into six tabs:
- Sandbox storage
- Web browsers
- Virtualized processes
- Privacy
- Exclusions
- Internet access
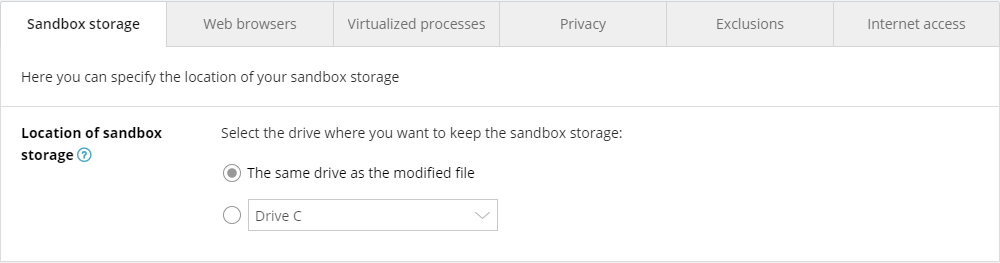
Sandbox Storage
Within this tab, you can specify where Sandbox storage is created, choosing either the same drive as the modified file or a different location.
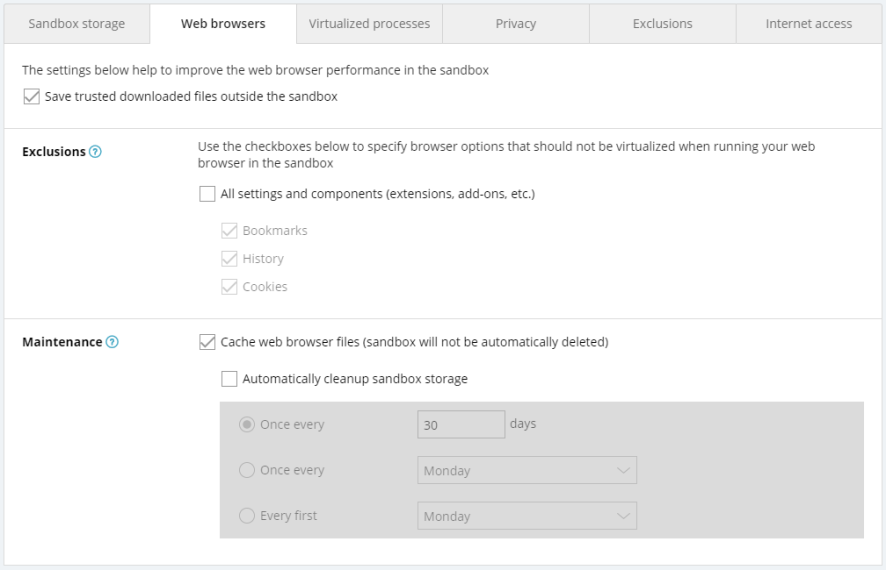
Web Browsers
The settings available here are designed to improve the sandboxed browser's performance. You can:
- Choose whether trusted downloaded files will be saved outside of Sandbox
- Exclude certain browser features from virtualization so that they are not deleted after closing Sandbox
- Cache virtualized files for web browsers only, and delete all other virtualized files
Exclusions can be applied to browser bookmarks, history, and/or cookies. If you, for example, exclude browsing history from virtualization, it will remain available when the browser is opened outside of Sandbox.
If you enable maintenance (caching only browser files), you will have the additional option to schedule automatic Sandbox storage cleanup.
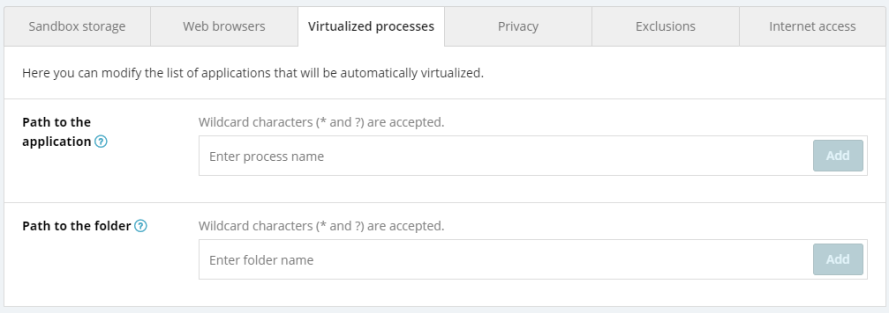
Virtualized Processes
In this section, you can set up a list of applications and/or folders that will automatically run in Sandbox.
Privacy
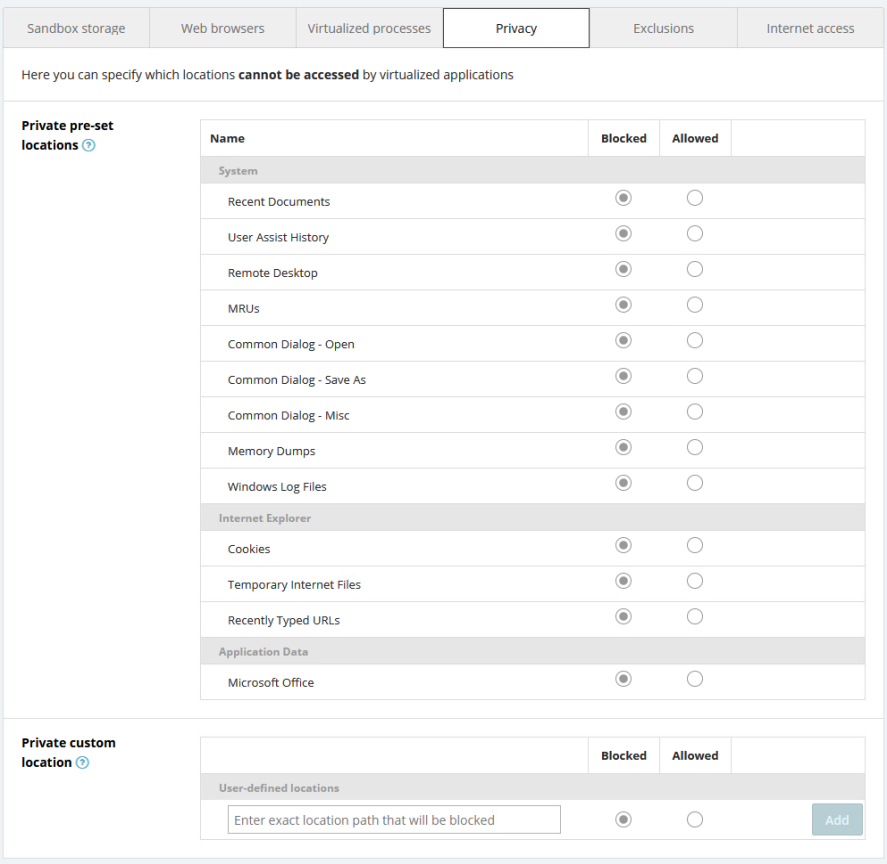
Within this tab, you can specify which locations can or cannot be accessed by virtualized applications. You can select from the listed preset locations or specify the locations manually. This provides an additional layer of protection, as the selected locations will be completely invisible to virtualized apps.
To add a custom location to the list, enter its path in the Private custom location section, choose whether the access to the location will be allowed or blocked, then click the Add button. Added paths can be edited/removed if needed.
Exclusions
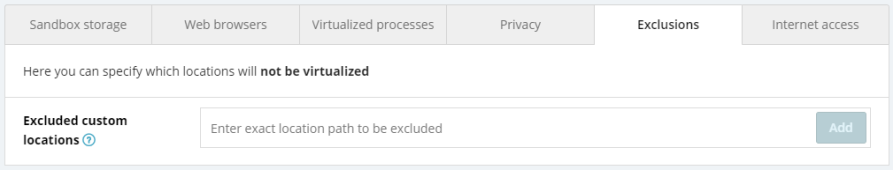
Here, you can configure the list of locations that are not virtualized by entering the exact file location path to be excluded. These exclusions will only apply when Sandbox is used to virtualize potentially infected files, and will ensure the specified locations are not brought into the virtualized environment.
To add a Sandbox exclusion to the list, enter its path in the Excluded custom locations section, then click the Add button. Added paths can be edited/removed if needed.
For more information on standard and component-specific exclusions, see
Internet Access
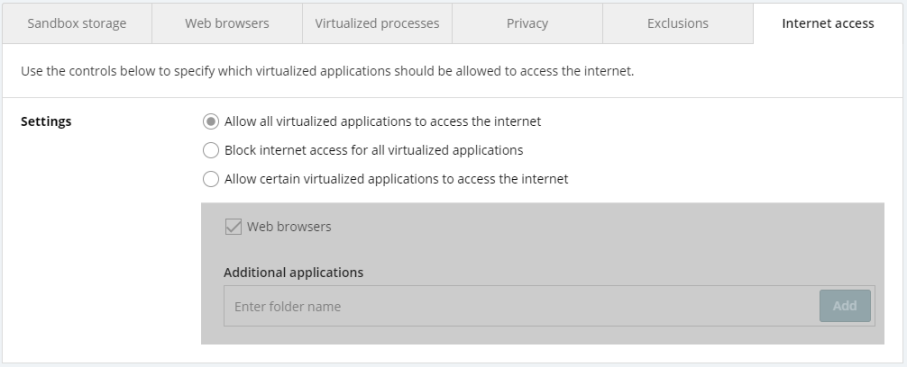
Here, you can specify whether to allow all/specific virtualized apps to access the internet or block internet access for all virtualized applications.
To allow internet access to specified apps only, select Allow certain virtualized applications to access the internet, enter the app path, then click the Add button (repeat the steps for each app you want to add). Added paths can be edited/removed if needed.
Ticking the Web browsers checkbox above the Additional applications list will allow browser apps to access the internet.
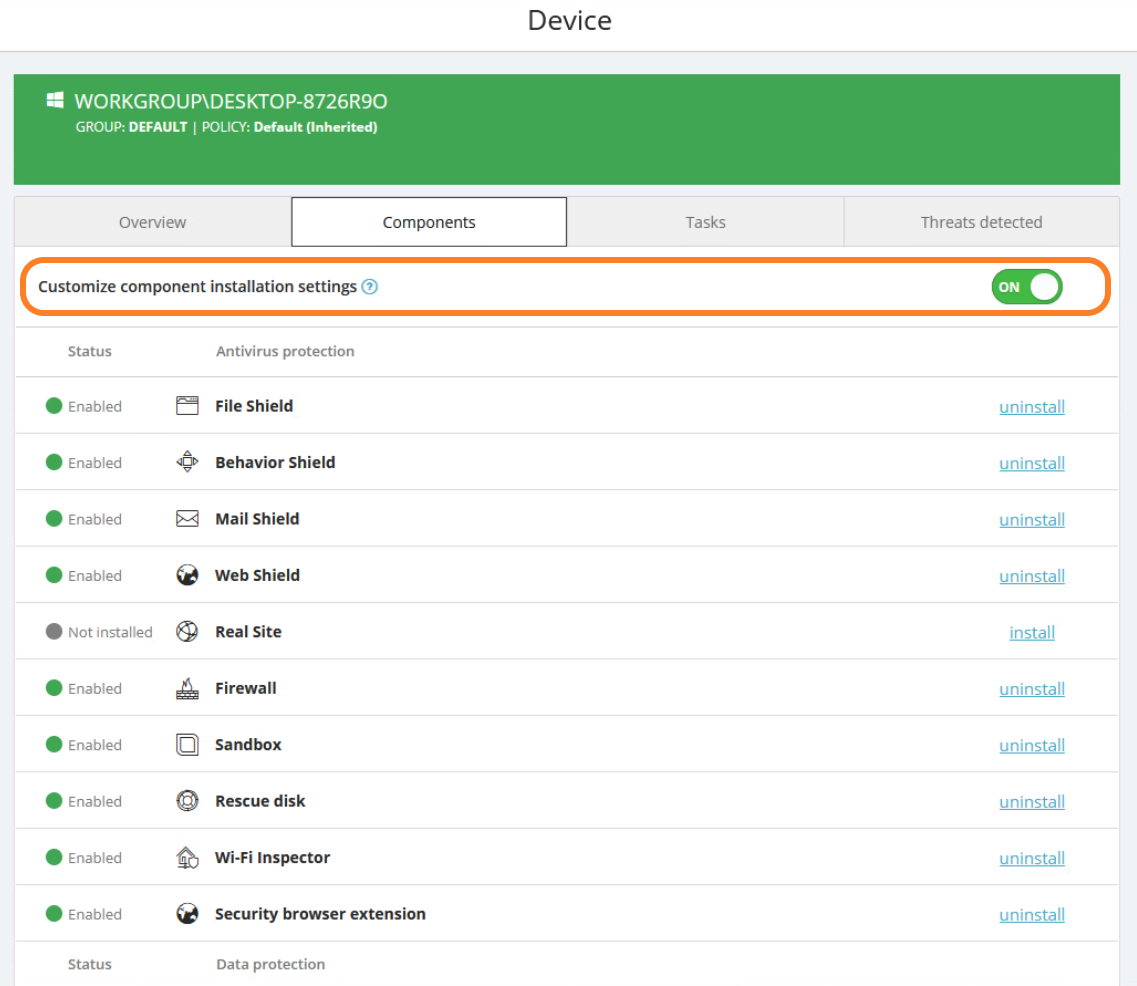
Overriding Policy Settings
Via the Components tab of a device, you can override its policy configuration for Sandbox by setting the Customize component installation settings toggle to ON and then clicking install/uninstall next to the component.
To learn more about policy overrides, see
Other Articles In This Section:
Exchange and SharePoint Protection
Components Without Customization Options in On-Premise Console
Related Articles: