PROXIMANOVA-LIGHT.OTF PROXIMANOVA-LIGHTIT.OTF PROXIMANOVA-EXTRABLD.OTF PROXIMANOVA-BOLD.OTFPROXIMANOVA-BLACK.OTF
Get this font in here!
This Article Applies to:
- Avast Business Hub
The Exchange component for Windows Servers is specifically meant to protect your Exchange Server from threats without interfering in its function. It scans and filters emails for viruses at the Exchange server level to help stop potential attacks before they spread to the network.
Supported Exchange Servers
Microsoft
Prerequisites
For
Recommended Antivirus Components
When installing servers in a business environment, please follow our guidelines in
Configuring Exchange Protection
To access Exchange settings:
- Open the Policies page
- Click the desired policy to open its Detail drawer
- Click the Settings tab, then Antivirus
- Under Data Protection, expand the Exchange section
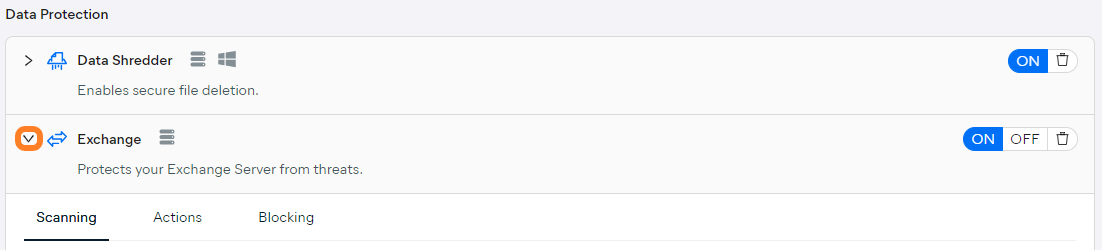
The available configuration options are grouped as follows:
- Scanning
- Actions
- Blocking
Scanning
Here, you can configure basic scanning parameters:
- Scan messages on-access: On-access scanner scans messages upon downloading, and remains active even if scanning messages in the background and proactive scanning options are off.
- Scan messages in the background (Exchange 2010 only): Background scanning works when an item that has not been scanned with the latest Avast virus definitions is encountered in the users’ mailbox folders. Scanning and searching for not examined objects runs in parallel. A specific low priority thread is used for each database, which guarantees other tasks (e.g. email messages storage in the Microsoft Exchange database) are always carried out preferentially.
- Enable proactive scanning (Exchange 2010 only): Proactive scanning works when an item is delivered to a folder, but a request has not been made by a client. As messages are submitted to the Exchange store, they enter the global scanning queue as low priority (maximum of 30 items). They are scanned on the first in, first out (FIFO) basis. If an item is accessed while still in the queue, it is changed to high priority.
- Scan at transport level: Enables scanning of emails at the Exchange Hub Transport level.
- Scan RTF message bodies: Enables scanning of messages in rich text format.
- Try to clean infected objects: infected objects will be cleaned (e.g. remove malicious code only); if unsuccessful, they will be removed.
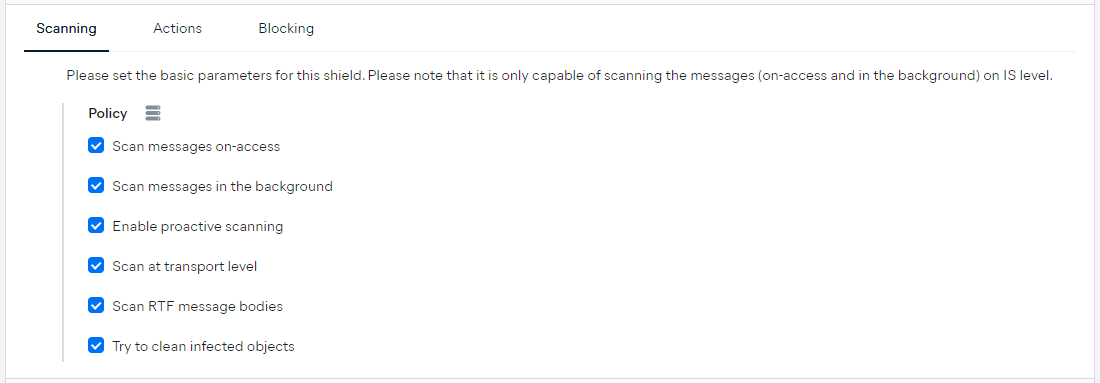
Note that Exchange Shield can only scan messages (on-access and in the background) on IS level.
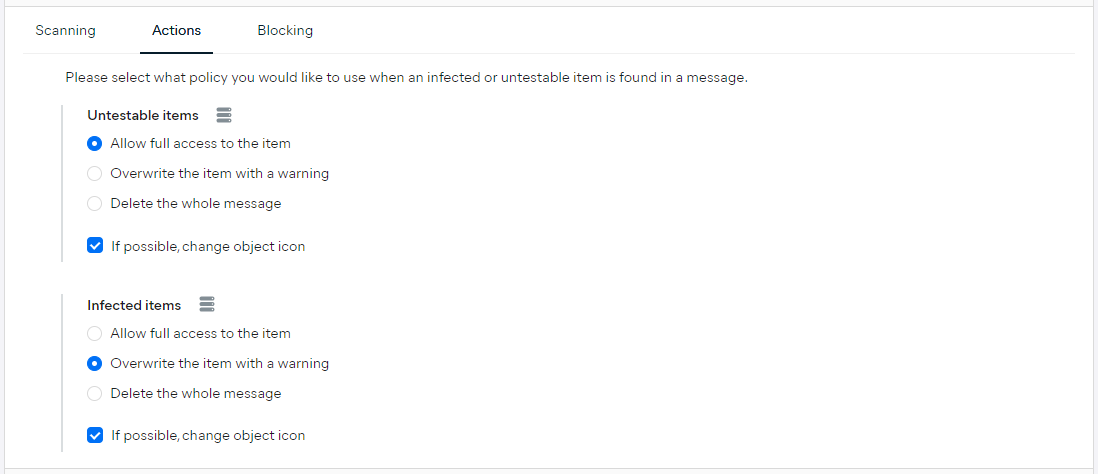
Actions
The Actions settings allow you to configure how untestable and infected items are handled. In both cases, you can choose to allow full access to the item, overwrite the item with a warning, or delete the whole message.
You can also change the infected object's icon (if possible).
Blocking
Use these settings to block attachments with specified filename masks (characters and wildcards used to match folder and file names) that are found in messages coming through Exchange.
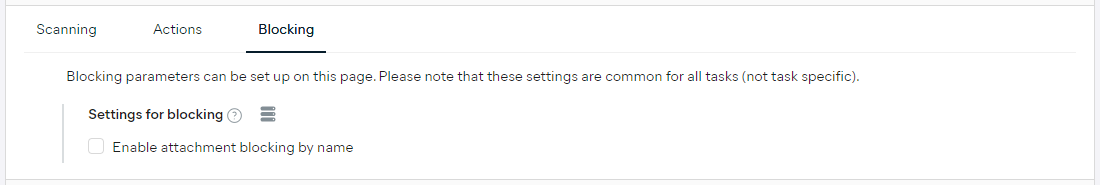
To configure attachment blocking:
- Tick the Enable attachment blocking by name checkbox
- Click the + Add mask button
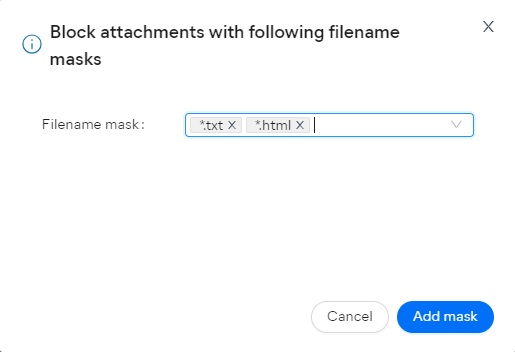
- Enter the desired filename mask(s) in the pop-up dialog
- Click Add mask
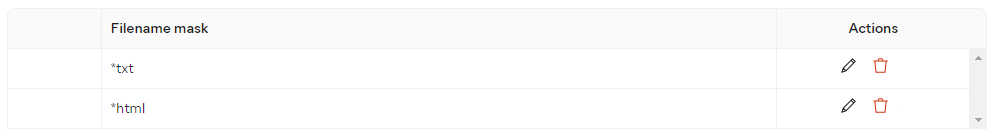
The list will then get populated with your entries, which you can edit/delete anytime if needed.
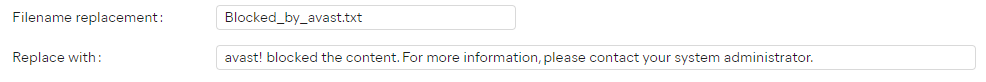
At the bottom of the settings, you can also choose what the file's name is replaced with, and the content of the .txt file that will replace the blocked file.
FAQ
 Does Exchange protect cloud/365 mailboxes?
Does Exchange protect cloud/365 mailboxes?
No, only on-premise Exchange.
 Does Exchange protect against spam?
Does Exchange protect against spam?
No, only viruses/malicious content.
 Why do some features only support Exchange 2010?
Why do some features only support Exchange 2010?
This is because VSAPI support was discontinued by Microsoft since Exchange 2013. Therefore, those features became unavailable.
 Should I run Mail Shield as well?
Should I run Mail Shield as well?
No, Mail Shield is only for workstation OS, only the Exchange component is required.
Other Articles In This Section:
Services and Components Without Customization Options in Business Hub
Related Articles: